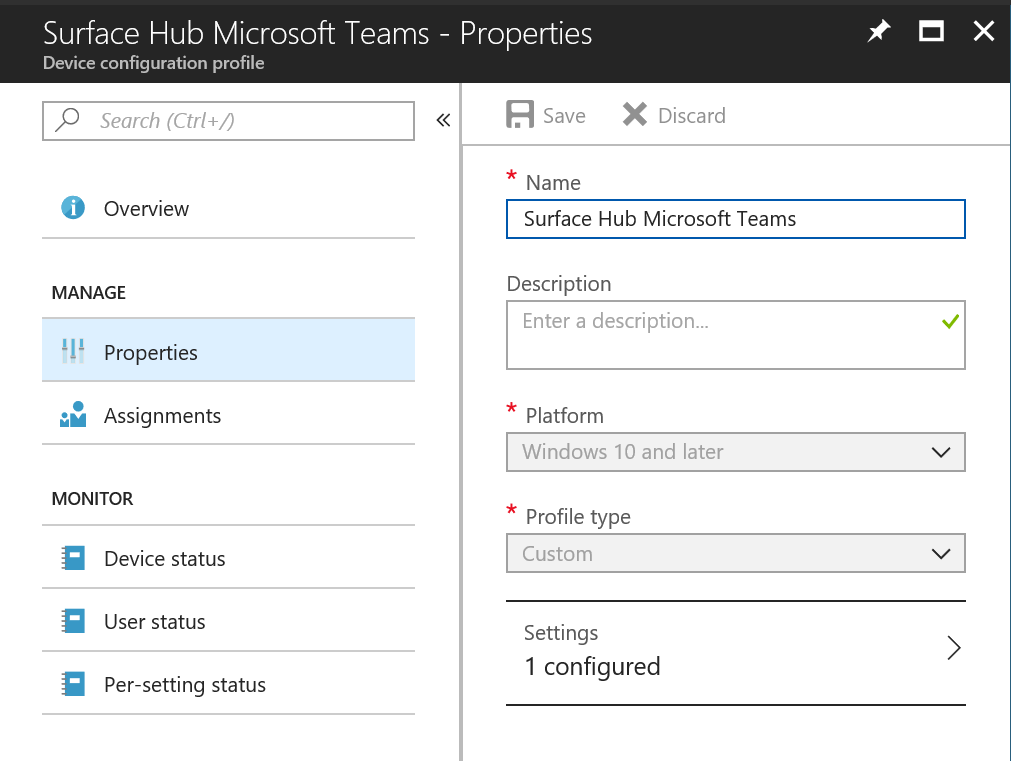
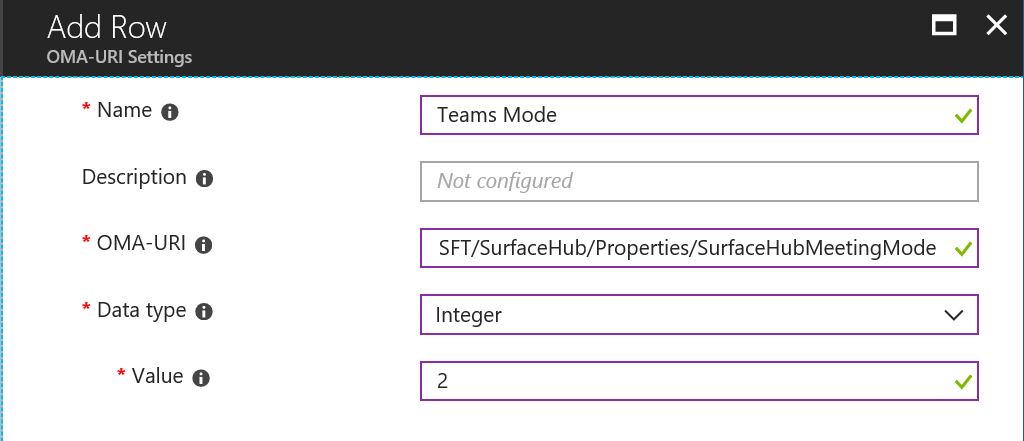
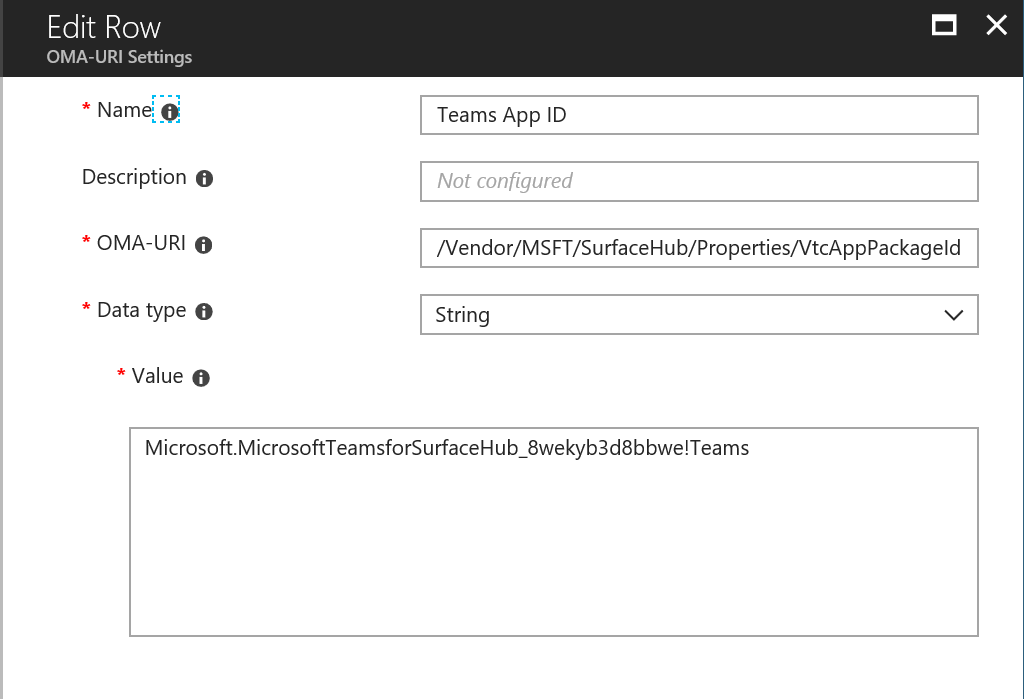
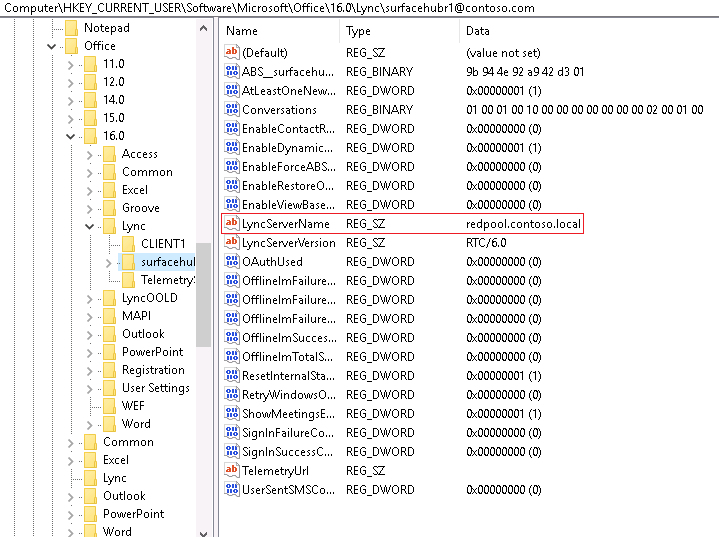
This gets even more challenging when working in a Multi-Domain or Mutli-Forest environment, where allowing users from different domains and forests to book resources on other domains.Let’s see if we can break that down in a way that makes sense:


(Going back to Windows Server 101, let’s recap what Active Directory Forest and Domains are…)
- Domains are container objects; They are a collection of administratively defined objects that share a common directory database, security policies, and trust relationships with other domains.
- Domain trees are collections of domains that are grouped together in hierarchical structures; When you add a domain to a tree, it becomes a child of the tree root domain. The domain to which a child domain is attached is called the parent domain.
- A forest is a complete instance of Active Directory; A forest acts is a container that houses all the domain containers for that particular Active Directory instance. A forest can contain one or more domain container objects. By default, information in Active Directory is shared only within the forest.
So basically, you can have multiple forests that have multiple domains in them. By default, a domain provides authentication and authorization services for all its accounts, in order to facilitate logons and single sign-on access control to shared resources within the boundaries of the domain.
Forests can be used to segregate domain containers into one or more unique DNS namespace hierarchies known as domain trees. Because the forest is a security boundary, each forest does not trust or allow access from any other forest by default.
If your environment has multiple forests such as a User forest and a Resource forest, you might want to check this article in the Surface Hub Admin Guide.
Nevermind the setup, how do we get collaboration working right?!
Let’s try to answer some of the common questions that we normally see:
– How would you handle booking hubs? If we tied all the hubs to one parent domain, would TNEF & and proper federation allow for any of the sub domains to book hubs?
First, allow your Surface Hubs to receive external meeting invites. This will allow users outside your Exchange Organization to invite the Hubs’ room mailboxes.
To enable that, run the following command against your Hubs:
Set-MailboxCalendarSettings HubRoom1@contoso.com –ProcessExternalMeetingMessages $True
TNEF configuration is not required for Surface Hub when sending meeting invites from remote domains. The Skype for Business client on the Hub can read the meeting url in the invite, and does not require the “winmail.dat” attachment in the invite header. If you’re using Skype Room Systems as well as Surface Hub – TNEF is required for SRS and can be configured using these instructions.
Federation is required and must be configured between both organizations for the Hub to join the meeting. Check with your Skype for Business admin that federation is enabled and add the remote domains if required:
New-CsAllowedDomain -Identity "fabrikam.com"
To further simplify the process, create a Mail Contact for the Hub in every remote organization so that users can easily find it and send it meeting invites:
New-MailContact -Name "Fabrikam Surface Hub 20" -ExternalEmailAddress "SurHub20@fabrikam.com"
Now for some context:

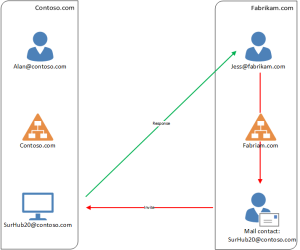
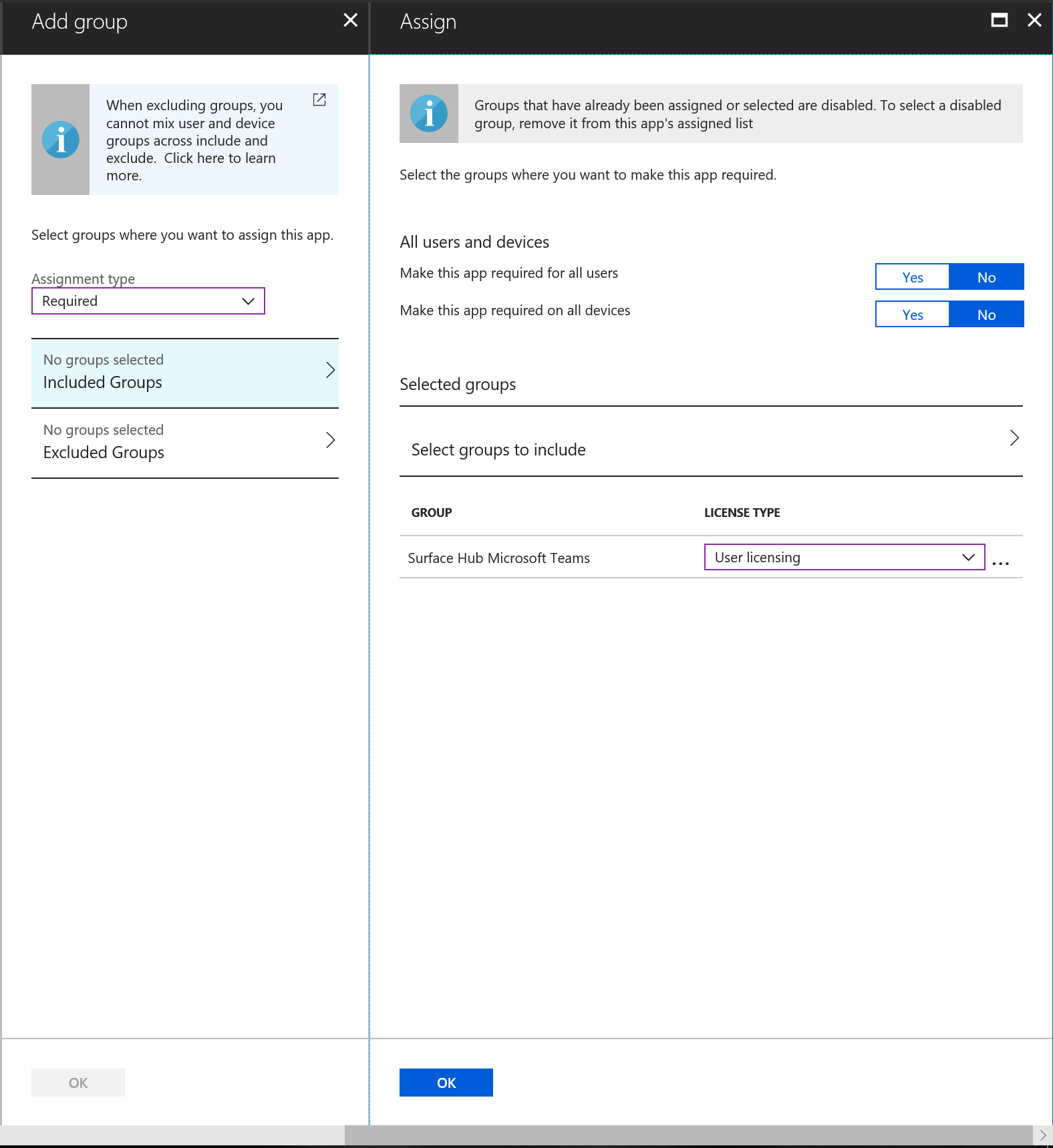
Diagram 1 above explains what happens when Jess from the Fabrikam domain wants to invite “Surface Hub 20” on the Contoso domain:
- Jess will use the Address Book in the Fabrikam domain to find the Mail contact for Surface Hub 20 in the Contoso Domain.
- The invite will be sent to SurHub20@contoso.com
- A response will be sent directly to Jess based on the resource availability.
This is common in multiple-domain environments where admins can create mail contacts for users in other domains.
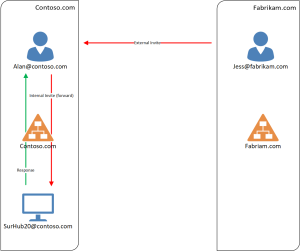

Diagram 2 above explains what happens when Jess from Fabrikam invites Alan from Contoso to a meeting, which Alan then forwards to “Surface Hub 20” in his organization:
- Jess sends a Skype Meeting invite to Alan.
- Alan forwards the meeting invite to “Surface Hub 20”.
- “Surface Hub 20” will accept or decline the meeting based on availability.
– Will users from any Office 365 tenant be able to login to “my files” on OneDrive?
Yes. Especially if your organization is using Office 365 and your environment is optimized for Office 365.
Any user can log on to their files on Office 365 once they authenticate, subject to their organization’s policies.
– Will users from any tenant\domain be able to Miracast?
Yes, Miracast does not require user authentication in order to project your screen to the Hub. Anyone with a Windows 10 device or a compatible device can project to the Hub.
For more information check the Surface Hub Admin Guide here.